IT Security Services
(877) AGILITY
All-Device IT Security ServicesWorkstations, Phones, & Servers
Agility Network Services, Inc. provides IT security services to protect your organization from cyber threats. With their desktop protection services, you can work with confidence. Your data is safe from attacks. Whether you run a small business or a large company, we can create a security plan for you.
Penetration Testing Services Perimeter / Firewall
Agility Penetration Testing for;
Penetration Testing for Applications
Why Us?

Pishing & Spear Pishing Testing
Cyclone End Point Security
Agility NETWORK Protection:
Identity Services
Business Challenges;
Proven Results Backed by Social Reviews!
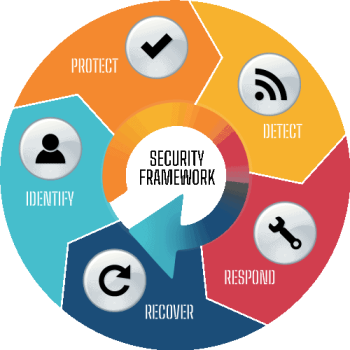
6 Areas of AttentionIT Security
- Audit
- Quote
- Installation
- Management
- Response
- Support
Agility knows the threats businesses face. It is a constant challenge: from hackers, malware, and other security risks. The need for endpoint security is as critical as malware and virus protection.
Luckily, Agility represents, installs, manages, and supports all three in a cohesive suite of best-of-breed endpoint software solutions. All of which are monitored and managed by a single pane of glass.
Agility’s IT Security SoftwareProduct and Solutions Details
A granular list of what is included through a non-exhaustive list. This list is more specifically tied to the remote monitoring and management threat protection. Information found further down such as Agility Network Services Client Information Portal listed in the next section.
Agent-based capabilities begin immediately upon deployment and activation of your Client-Specific Policies. Reporting of mitigation of threats available upon request.
Industry-Leading Functionality Performance (PDF of Report Available on Demand)
- Optional Management for All Endpoints of Infrastructure Devices
- Firewall Monitoring and Management of External Threats
- Client-Specific Maintenance and Scan Schedules (hour-by-hour, month, and year)
- Network Assessment Services (as pre-Client or Client)
- Virtualization Technology implementation Support and Managemen
- Strategic Support Teams / vCIO strategic support
- Work Type-Specific Consulting Teams
- Project management and execution teams
- Office 365 Licensing Consulting and Procurement
- Vendor Management for Hardware and Software
- Vendor Management for each I.T. Niche Including Internet-Based SaaS and Vendors Needed “Remote Hands”
- All Cloud Infrastructure or Cloud Operating Systems (co-location, VPN’s, disparate users, disparate Web-Connected Business Unit Needs)
- Cloud Computing Migrations Planning, Implementation, and Cloud Infrastructure Management.
(on-site, virtual OS, and Cloud-Based)
- Help Desk 24 x 7 x 365
- On-site Support Services
- Remote Support Services
- Threat Protection and Reporting in Agility PSA*
- Issues Resolution Documentation Available
- Ticket Escalation Processes per SLA per Type
- Completed Ticketing Reports
- Real-Time, at all times, Remote Monitoring
- On-Going Growth of Automated Mitigation Scripts
- Windows licensing expertise
- Third-Party application upgrade services
- Full Scripting Capabilities
- Real-Time Network Traffic Monitoring
- Documentation Technology
- Asset Management (Stock and Client-Tailored)
- Workstation Antivirus / Antimalware Threat Management
Industry-Leading Functionality Performance (PDF of Report Available on Demand)
- Constant Realtime Endpoint Protection
- Internet Browser and Operating System Shield
- Virus Threat Shield
- Malware Threat Shield
- Heuristics Threat Protection
- Self-Protection Ensure Continuous Protection
- Realtime Shield
- Behavior Shield Analysis of Each Application
- OS Core Shield
- Web Threat Shield
- Identity Shield
- Data Monitor All Outbound Ports
- Untrusted Process Monitoring
- Windows Firewall Integration
- Inbound Traffic Threat Shield
- System Optimization (reg, OS Cleanup)
- Clean Integration into PSA
- Agility Professional Services Automation Alerting and Report
Integrated IT Security Services: IT Security Services
Threat Detection & Response
Agility Network Services, Inc. advanced threat detection systems monitor your network 24/7, identifying potential vulnerabilities and responding to threats in real-time. This proactive approach ensures that any suspicious activity is addressed immediately, minimizing the risk of data breaches and other security incidents.
Desktop Malware & Virus Protection
We provide comprehensive desktop protection to safeguard your devices from malware and viruses. Agility Network Services, Inc. solutions include regular updates and scans to ensure that your systems are always secure. With Agility Network Services, Inc. desktop protection services, you can work with confidence. Your data is safe from harmful attacks.
Customized Security Solutions
At Agility Network Services, Inc., we recognize that every business is unique. That’s why we offer customized security solutions that align with your specific operational requirements. No matter if you run a small business or a large company, we can create a security plan for you. It will match your needs and budget.
Ongoing Support & Training
In addition to Agility Network Services, Inc. security services, we also provide ongoing support and training for your staff. We believe that education is a key component of cybersecurity. We help create a culture of security in your organization. We do this by giving your team the knowledge and tools they need to recognize and respond to threats.
24x7x365 IT Security Services
Agility has always addressed the growing security threat to our networks. We blend dynamic technology and security solutions, catering to the various needs of small and medium businesses. Our wide range of I.T. Network Security Services includes network operations, cyber threat intelligence, anti-phishing vulnerability assessment, and many more. We extend our network security services with 24×7 support.
Why Only Agility Network?
Don’t be an easy target for attackers. Prevent threats and leverage our superior monitored and managed security services. Combined with advanced technology and security expertise, Agility operates to protect your devices and data. Providing continuous security monitoring, our intelligent advancements can detect and respond to the threats you can’t prevent.
Chicago IT Services
Comprehensive I.T. Services for Mid-Market and SMB Businesses and NFP Firms
Business Continuity: Back-Up/Disaster Recovery/Fail-Over – I.T. Security: Anti-Virus & Anti-Malware /Cylance Protect End-Point Security / On-Site MSSP Consulting Firewall Penetration Testing / Cloud Migration Services / Email Migration Services / Microsoft Azure Server Migration / Desktop Virtualization / Virtual Desktop Interface (VDI) / Emergency Network Support / IT Audits & Assessments / Systems Virtualization & Consolidation / Hyper-V / Vmware / Wireless Products or Services / Assessments / Installation / Management / Extensive Wireless Experience – Office 365 Microsoft Office Application Suite / Excel/Word/OneDrive for Business/SharePoint Online/Skype for Business/Storage/Visio / Managed Services Provider
IT Security Services FAQs

Our desktop protection services help ensure that your data is secure from various cyber threats, allowing you to work with confidence. This service includes real-time monitoring and updates to protect against malware and other vulnerabilities.
Penetration testing simulates cyber attacks on your systems to identify vulnerabilities before malicious actors can exploit them. It’s crucial for understanding your security posture and ensuring your defenses are robust.
Phishing is a broad attempt to trick individuals into revealing sensitive information, usually through mass emails. Spear phishing is more targeted, focusing on specific individuals or organizations. Our testing services help identify weaknesses in your defenses against both.
We recommend conducting penetration tests at least annually, or more frequently if you make significant changes to your IT infrastructure or experience a security incident.
If you suspect a phishing attack, do not click on any links or download attachments. Report the email to your IT department or our support team immediately for further investigation.
Our identity services help manage user identities and access controls, ensuring that only authorized personnel have access to sensitive information and systems, reducing the risk of insider threats and unauthorized access.
Comprehensive I.T. Services
for Mid-Market and SMB Businesses and NFP Firms
Agility has been consistently providing services to Small- and Mid-Sized Business of All Types – Corporations and Non-Profits that are nearly Industry Agnostic Horizontal Demographic rather than One or Two Verticals.
Managed Services
Powerful software agents, cyber-protection & network-wide software allowing your firm to have Agility more efficiently automate consistent service delivery through high-end consultants almost immediately.
IT Security
There is Not One Part of Any Network Including the Users Where Security is Not Top-of-Mind. as Broad as Anti-Virus Desktop Management to High-End Pen Testing.
Cloud Services
Cloud decisions and execution from highly experienced consultants at Agility are critical for migrations (to/from), secure throughput especially with service quality demands from more devices per employee.
Continuity
Backup Solutions, Disaster Recovery and Fail-Over Make-Up Our Business Continuity Approach Template. Agility has outstanding solutions.
IT System Audits and Assessments
We offer assessments, services, and features important to leaders such as executive breakdown of risks, outstanding issues, and remediation steps.
Microsoft O365
From hosted email to complete cloud solutions, we will customize Office 365 for your business needs.
Systems Virtualization & Consolidation
We offer a variety of desktop and server virtualization consulting services that help our clients’ increase their ROI.
Emergency Support Network
Whether you are an existing client or a small to midsize business looking for immediate service, we can help!
Wireless Products & Support
Wireless internet working is becoming a ubiquitous component of business environments and has been evolving faster than its copper/wired counterparts.
Project Services On-Site & Remote
Peruse the component parts of services offered or use to determine the capacity in which your firm needs Agility to fullfill.
Pen Testing Services
Most major business-class firewalls (each manufacturer is listed) allows quick-turn on quotes. Processes, pdf forms, and services at-the-ready
Acute IT Disruptions
When the unexpected occurs, a call to business development routes your firm to correct people for quick turn-a-round I.T. services – should services fit said urgent need.
Microsoft Azure Migrations
Migration To and From the Cloud. As a Gold Microsoft reseller, not only license fulfillment, not just services, allows trust in services of strategy or execution post-decision.
Desktop Virtualizations
One of the ambitions of Managed Services, long before it was even called that, was a Virtualized or a Hosted Desktop.
Computer Network Administration
Get Started Here:
Request a general IT evaluation or an IT Security evaluation and receive a no-obligation consultation and quote without charge. We’ll call you back to schedule a time with the appropriate IT Consultant/Engineer. This allows you to meet to potential team.
