Security of any kind begins with an understanding of your attackers and their approach. Especially in the cyber-security space, attackers are sophisticated and unpredictable. Agility’s is a more vigilant approach to Penetration Testing Services, designed to mimic the black-hat threats we see gaining access to so many organizations today, then build a plan of action to defend.
Agility Penetration Testing;
Threats are not limited to an organizations network infrastructure. The application space is another arena where would be attackers can wreak havoc. Whether the application is purchased or built by your organization, vulnerabilities can get exposed. Unlike infrastructure, applications tend to change more often, inadvertently transforming a secure application to one more vulnerable. Consequently, security becomes a moving target demanding regular review with its own penetration testing regime or software development life cycle support.
Agility will build a specific campaign designed to expose your organization, your IT policy adherence and general understanding of these threats by your staff. Subsequent changes in technology, threat detection and staff training are common next steps to help secure your corporate resources.
Agility Managed Services are when a firm like Agility takes over the management of your computer network. The Agility team watches and manages your network using the latest monitoring and management tools. Our staff includes a help desk, staff consultants, Senior Consultants and vCIO’s to address the entire scope of your IT needs.”
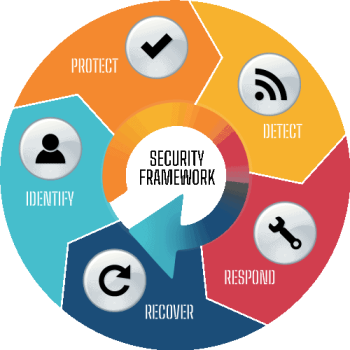
We understand that in today’s digital landscape, businesses face constant challenges from hackers, malware, and other security risks. That’s why we offer a robust suite of managed services tailored to meet your specific needs & budget.
A granular list of what is included through a non-exhaustive list. This list is more specifically tied to the remote monitoring and management threat protection. Information found further down such as Agility Network Services Client Information Portal listed in the next section.
Agent-based capabilities begin immediately upon deployment and activation of your Client-Specific Policies. Reporting of mitigation of threats available upon request.
Industry-Leading Functionality Performance (PDF of Report Available on Demand)
(on-site, virtual OS, and Cloud-Based)
Industry-Leading Functionality Performance (PDF of Report Available on Demand)
Threat Detection & Response
Agility Network Services, Inc. advanced threat detection systems monitor your network 24/7, identifying potential vulnerabilities and responding to threats in real-time. This proactive approach ensures that any suspicious activity is addressed immediately, minimizing the risk of data breaches and other security incidents.
Desktop Malware & Virus Protection
We provide comprehensive desktop protection to safeguard your devices from malware and viruses. Agility Network Services, Inc. solutions include regular updates and scans to ensure that your systems are always secure. With Agility Network Services, Inc. desktop protection services, you can work with confidence. Your data is safe from harmful attacks.
Customized Security Solutions
At Agility Network Services, Inc., we recognize that every business is unique. That’s why we offer customized security solutions that align with your specific operational requirements. No matter if you run a small business or a large company, we can create a security plan for you. It will match your needs and budget.
Ongoing Support & Training
In addition to Agility Network Services, Inc. security services, we also provide ongoing support and training for your staff. We believe that education is a key component of cybersecurity. We help create a culture of security in your organization. We do this by giving your team the knowledge and tools they need to recognize and respond to threats.
24x7x365 IT Security Services
Agility has always addressed the growing security threat to our networks. We blend dynamic technology and security solutions, catering to the various needs of small and medium businesses. Our wide range of I.T. Network Security Services includes network operations, cyber threat intelligence, anti-phishing vulnerability assessment, and many more. We extend our network security services with 24×7 support.
Why Only Agility Network?
Don’t be an easy target for attackers. Prevent threats and leverage our superior monitored and managed security services. Combined with advanced technology and security expertise, Agility operates to protect your devices and data. Providing continuous security monitoring, our intelligent advancements can detect and respond to the threats you can’t prevent.
Business Continuity: Back-Up/Disaster Recovery/Fail-Over – I.T. Security: Anti-Virus & Anti-Malware /Cylance Protect End-Point Security / On-Site MSSP Consulting Firewall Penetration Testing / Cloud Migration Services / Email Migration Services / Microsoft Azure Server Migration / Desktop Virtualization / Virtual Desktop Interface (VDI) / Emergency Network Support / IT Audits & Assessments / Systems Virtualization & Consolidation / Hyper-V / Vmware / Wireless Products or Services / Assessments / Installation / Management / Extensive Wireless Experience – Office 365 Microsoft Office Application Suite / Excel/Word/OneDrive for Business/SharePoint Online/Skype for Business/Storage/Visio / Managed Services Provider

Penetration testing is essential for applications because vulnerabilities can arise from frequent updates and changes. Regular testing helps identify potential security flaws before attackers can exploit them, ensuring the application remains secure over time.
While infrastructure penetration testing focuses on network and system vulnerabilities, application penetration testing targets the specific risks within the application itself. This includes examining code, configurations, and user interactions to uncover security weaknesses unique to the application environment.
All applications, whether purchased or developed in-house, should undergo penetration testing. This includes web applications, mobile apps, and APIs, as they are all potential entry points for attackers.
Given that applications can change frequently, it’s advisable to conduct penetration testing regularly—ideally after significant updates, during the software development lifecycle, or at least annually—to ensure ongoing security.
Organizations can expect detailed documentation outlining identified vulnerabilities, risk assessments, and actionable recommendations for remediation. This helps prioritize security efforts and enhances the overall security of the application.
Agility has been consistently providing services to Small- and Mid-Sized Business of All Types – Corporations and Non-Profits that are nearly Industry Agnostic Horizontal Demographic rather than One or Two Verticals.
Powerful software agents, cyber-protection & network-wide software allowing your firm to have Agility more efficiently automate consistent service delivery through high-end consultants almost immediately.
There is Not One Part of Any Network Including the Users Where Security is Not Top-of-Mind. as Broad as Anti-Virus Desktop Management to High-End Pen Testing.
Cloud decisions and execution from highly experienced consultants at Agility are critical for migrations (to/from), secure throughput especially with service quality demands from more devices per employee.
Backup Solutions, Disaster Recovery and Fail-Over Make-Up Our Business Continuity Approach Template. Agility has outstanding solutions.
We offer assessments, services, and features important to leaders such as executive breakdown of risks, outstanding issues, and remediation steps.
From hosted email to complete cloud solutions, we will customize Office 365 for your business needs.
We offer a variety of desktop and server virtualization consulting services that help our clients’ increase their ROI.
Whether you are an existing client or a small to midsize business looking for immediate service, we can help!
Wireless internet working is becoming a ubiquitous component of business environments and has been evolving faster than its copper/wired counterparts.
Peruse the component parts of services offered or use to determine the capacity in which your firm needs Agility to fullfill.
Most major business-class firewalls (each manufacturer is listed) allows quick-turn on quotes. Processes, pdf forms, and services at-the-ready
When the unexpected occurs, a call to business development routes your firm to correct people for quick turn-a-round I.T. services – should services fit said urgent need.
Migration To and From the Cloud. As a Gold Microsoft reseller, not only license fulfillment, not just services, allows trust in services of strategy or execution post-decision.
One of the ambitions of Managed Services, long before it was even called that, was a Virtualized or a Hosted Desktop.
Request a general IT evaluation or an IT Security evaluation and receive a no-obligation consultation and quote without charge. We’ll call you back to schedule a time with the appropriate IT Consultant/Engineer. This allows you to meet to potential team.
© 2025 Agility Network Services, Inc. All Rights Reserved.